As an app developer, ensuring the security of your users’ data is paramount. With the rising threat of cyber attacks, implementing robust authentication measures is non-negotiable. One of the most effective ways to fortify your app’s security is through multi-factor authentication (MFA). By requiring users to provide multiple forms of verification, MFA adds an extra layer of protection against unauthorized access. Let’s delve into the various types of multi-factor authentication methods you can integrate into your app.
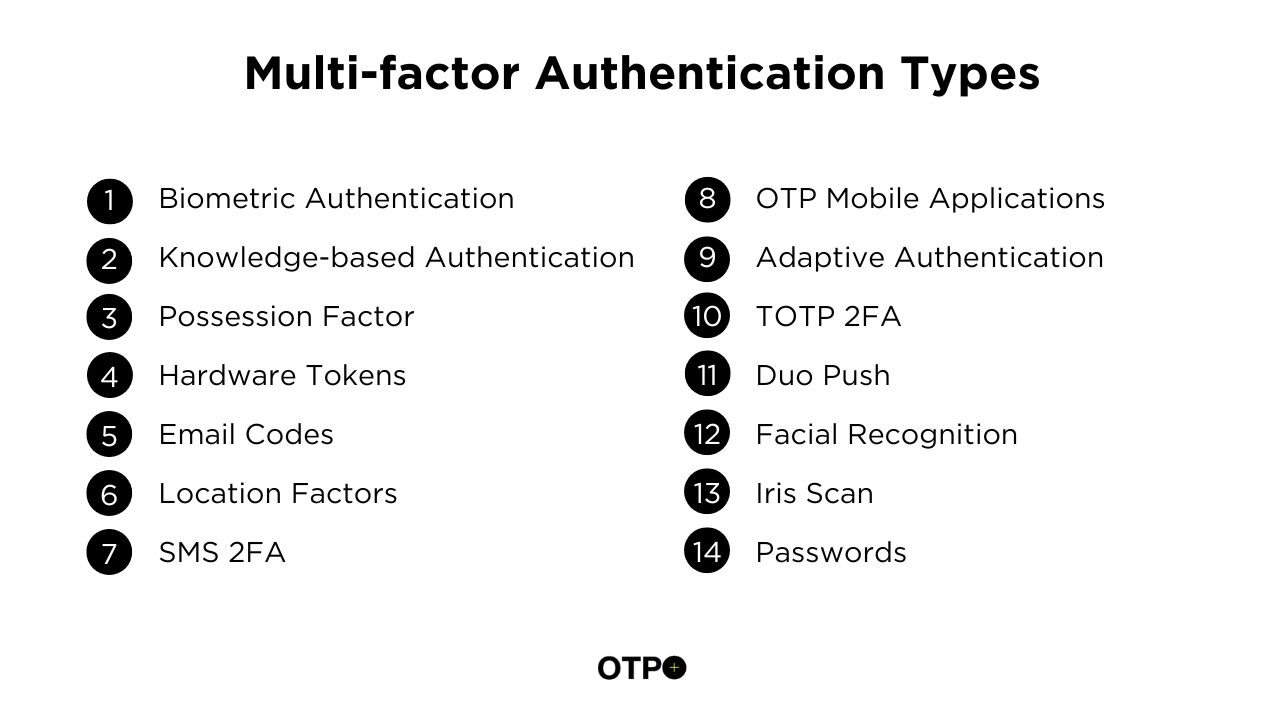
Multi-factor Authentication Types
1. Biometric Authentication
Consider integrating biometric authentication features such as fingerprint or facial recognition into your app. These unique biological traits offer a high level of security and enhance user convenience.
2. Knowledge-based Authentication
Utilize knowledge-based authentication methods like passwords or PINs. However, ensure that users are encouraged to create strong, unique passwords to mitigate the risk of brute force attacks.
3. Possession Factor
Incorporate possession-based authentication by leveraging hardware tokens or mobile devices. These tokens generate one-time passwords (OTPs), adding an extra layer of security.
4. Hardware Tokens
Explore the option of integrating support for hardware tokens such as key fobs or USB tokens. These physical devices provide an additional level of security and are resistant to hacking attempts.
5. Email Codes
While not the most secure option, consider offering email-based verification codes as an additional authentication factor. However, advise users to exercise caution when relying solely on email codes due to their susceptibility to breaches.
6. Location Factors
Implement location-based authentication to verify users based on their geographical location. However, be mindful of user privacy concerns and provide options for users who frequently travel or use VPNs.
7. SMS 2FA
Although widely used, SMS-based authentication has its limitations, particularly susceptibility to SIM swapping attacks. Consider offering SMS 2FA as an option but encourage users to explore more secure alternatives.
8. Standalone OTP Mobile Applications
Support standalone OTP mobile applications like Google Authenticator or Microsoft Authenticator. These apps generate one-time passwords directly on users’ mobile devices, enhancing security and convenience.
9. Adaptive Authentication
Explore adaptive authentication solutions that dynamically adjust the authentication process based on various factors such as user behavior and device characteristics. This proactive approach helps in detecting and preventing suspicious login attempts.
10. TOTP 2FA
Integrate support for Time-based One-Time Password (TOTP) authentication, commonly used in conjunction with mobile authentication apps. TOTP offers enhanced security by generating OTPs that are valid for a short period.
11. Duo Push
Consider implementing Duo Push, where users receive a push notification on their mobile devices to approve or deny login attempts. This method offers a seamless user experience while maintaining security.
12. Facial Recognition
Explore the integration of facial recognition technology to verify users’ identities through camera capture. Ensure transparency and user consent regarding the use of facial data to address privacy concerns.
13. Iris Scan
For high-security applications, consider incorporating iris scanning technology to authenticate users based on unique iris patterns. This method offers an exceptionally high level of security but may require specialized hardware.
14. Passwords
While traditional passwords remain prevalent, encourage users to supplement them with additional authentication factors for enhanced security. Provide guidance on creating strong passwords and educate users on the importance of password hygiene.
Here is a detailed blog to understand multi-factor authentication using examples.
Conclusion
In conclusion, as an app developer, implementing multi-factor authentication is crucial for safeguarding your users’ data and maintaining their trust. By offering a variety of authentication methods and staying abreast of emerging technologies, you can stay one step ahead of cyber threats and ensure a secure user experience for your app. Remember to prioritize usability without compromising on security, and continuously evaluate and update your authentication mechanisms to adapt to evolving threats.