If you’re developing applications, you know that managing user identities and access control is crucial. This is where Keycloak can be a game-changer. But what exactly is Keycloak, and how can it simplify your development process? Let’s break it down.
What is Keycloak?

Keycloak is an open-source Identity and Access Management (IAM) solution created by Red Hat. It’s designed to provide authentication and authorization services to applications and services. Think of it as a tool that handles user logins, roles, and permissions, so you don’t have to build those features from scratch.
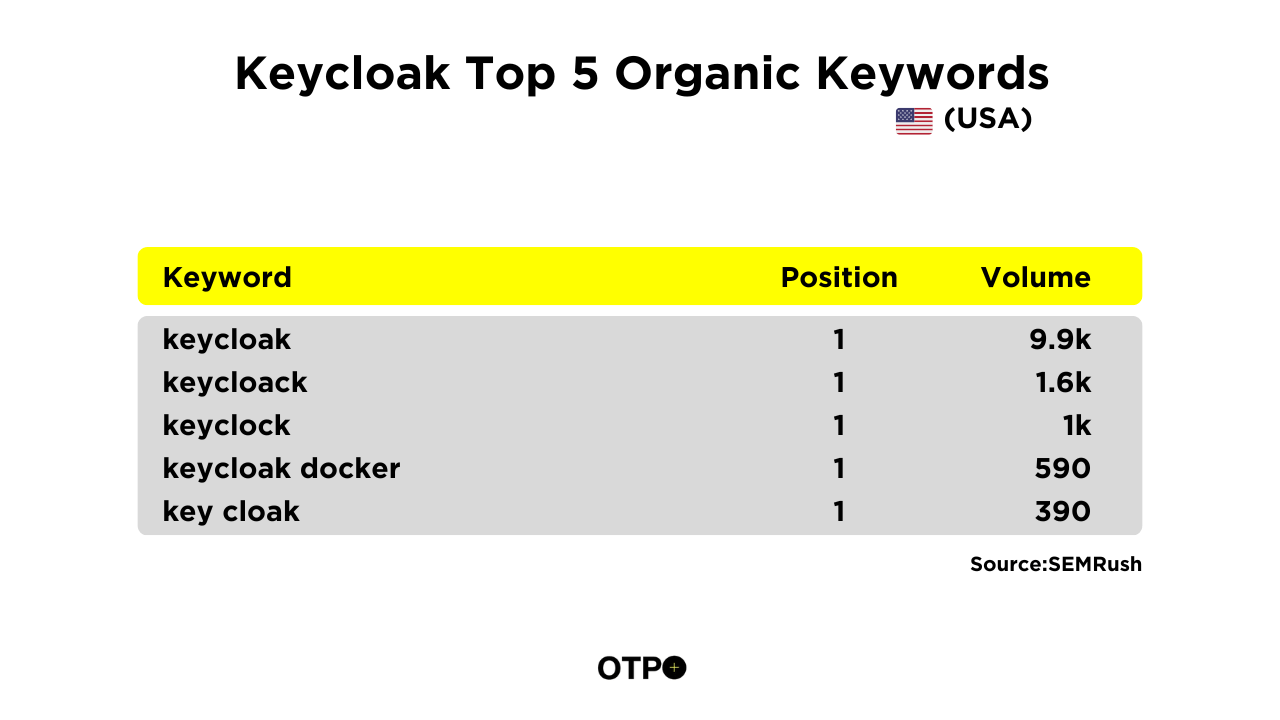
In terms of user base, it had 144k organic monthly traffic in June 2024 (Data from Semrush) (SEMRush is the 2nd most trusted SEO tool for analize the data). The amazing part is that it is increasing daily.
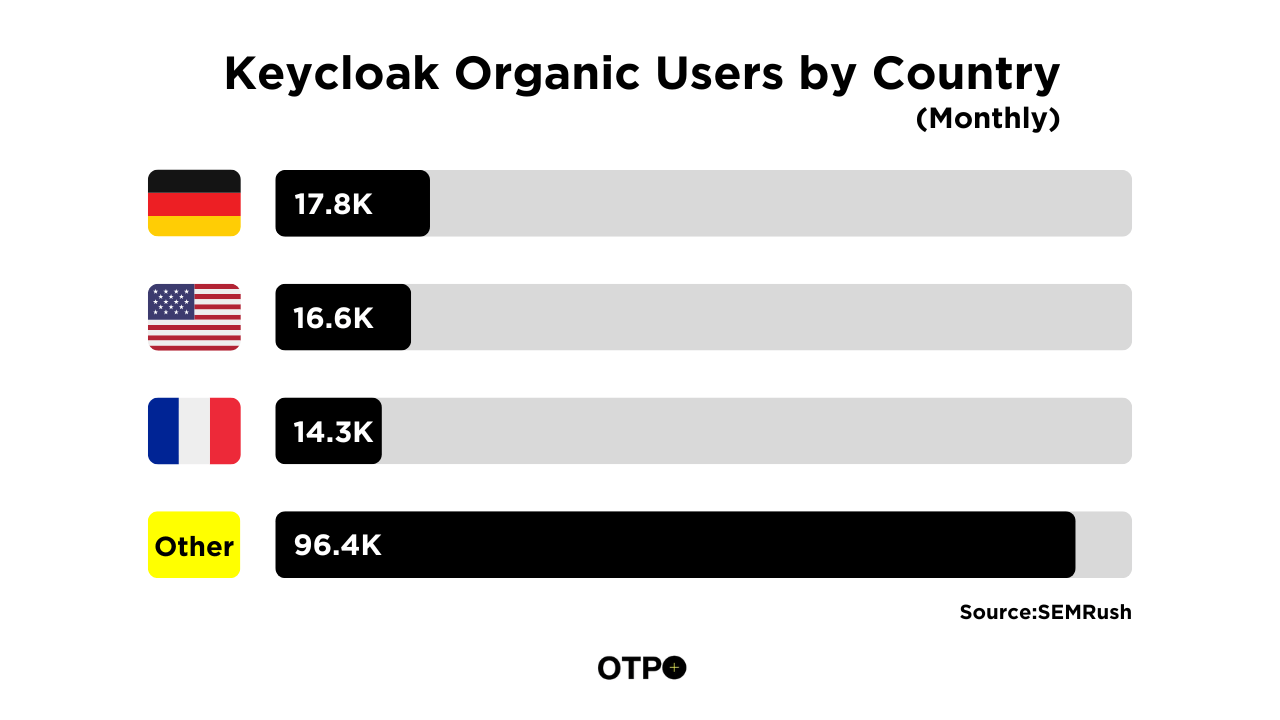
And more than 15000 users used to land on Keycloak using their brand name “Keyckoak” from the world. Here are the top 5 USA organic keywords that we have collated using SEMRush.
Keycloak Stats by OTP+
Based on our resource and research team we have collected some data that can help you undersatend how Keycloak is dominating in it’s domain.
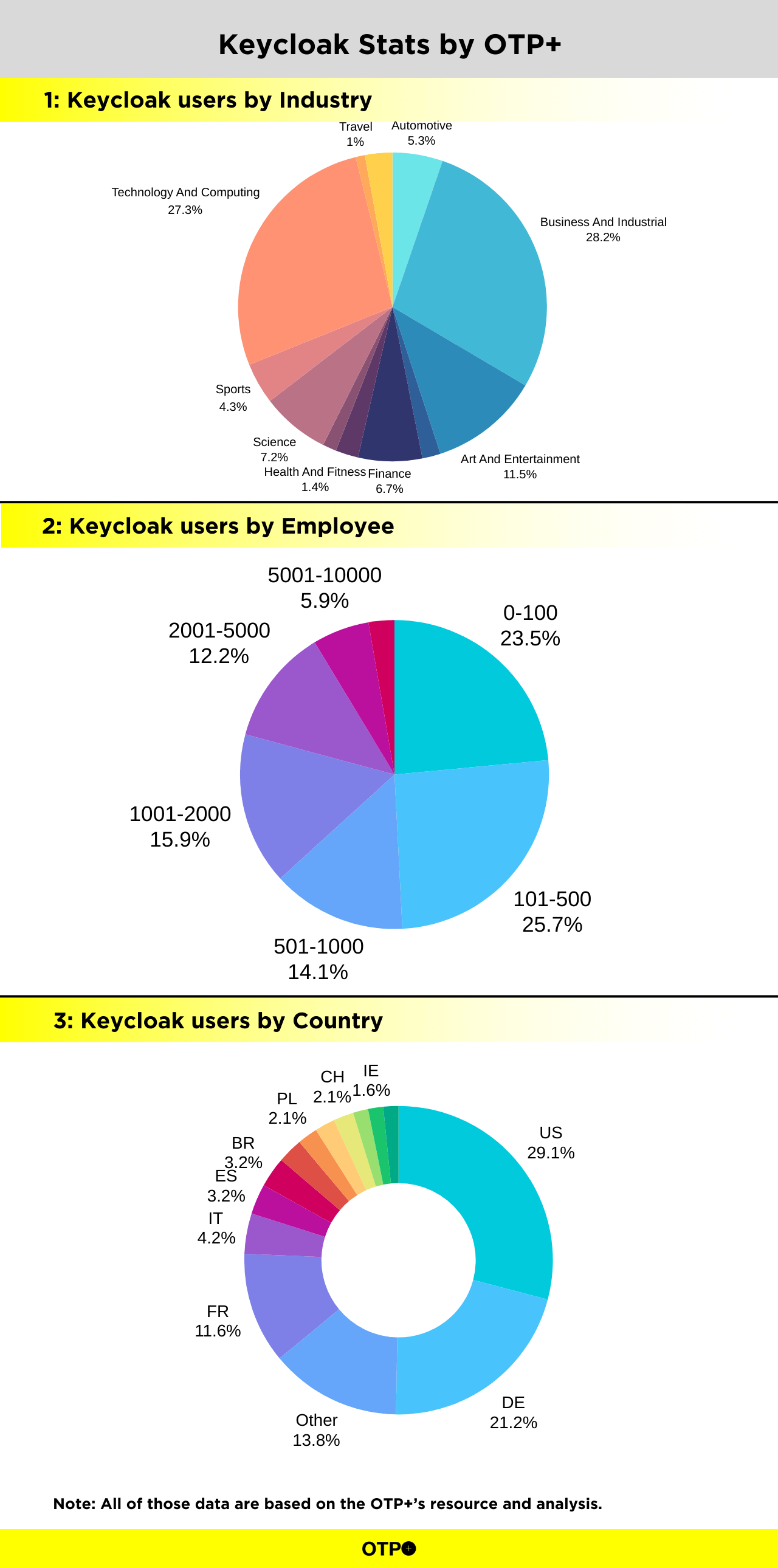
Here are some Key points
- Companies who are useing Keycloak, 27% belongs from Technology Industry.
- 25% of the Keycloak user companies are having employees in between 100 to 500
- 6% of the Keycloak user companies are having employees in between 5000 to 10000
- Keycloak have 29%users from USA and 21% from Germany
Key Features of Keycloak
Keycloak offers a range of features that can streamline your development process:
- Single Sign-On (SSO): Users log in once and gain access to multiple applications.
- Identity Brokering and Social Login: Users can log in using social media accounts or other identity providers.
- User Federation: Connects to existing user directories like LDAP or Active Directory.
- Role-Based Access Control (RBAC): Manages user permissions based on roles.
- OAuth2 and OpenID Connect Support: Implements these protocols for secure authentication.
Why Use Keycloak?
Benefits of Using Keycloak in Your App
- Streamlined Authentication and Authorization: Keycloak takes care of the complex stuff, letting you focus on your app.
- Enhanced Security: Supports various security protocols, keeping your apps secure.
- Scalability: Handles large user bases for small and large organizations.
- Customization: Tailor it to fit your specific needs with extensive customization options.
Comparison with Other IAM Solutions
Keycloak stands out because it’s open-source, highly flexible, and comes with a comprehensive feature set. Unlike some proprietary solutions, you can customize and extend Keycloak as much as you need. Here is an in-depth guide on Keycloak alternatives.
Keycloak Architecture
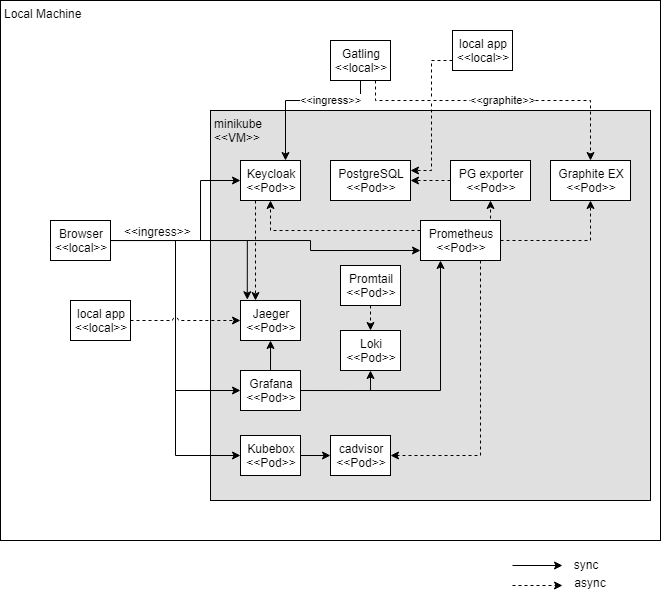
Components of Keycloak
- Keycloak Server: The main component providing authentication and authorization.
- Admin Console: A web interface for managing users, roles, and configurations.
- User Account Console: Where users manage their accounts.
- Adapters: Libraries will integrate Keycloak with various applications.
How Keycloak Works
Keycloak handles application authentication requests, validates credentials, and issues tokens granting access to resources. It supports multiple authentication methods, such as username/password, social logins, and third-party identity providers.
Setting Up Keycloak
Installation Process
Getting Keycloak up and running is straightforward:
- Download Keycloak: Get the latest version from the official site.
- Install Java: Make sure Java is installed on your server.
- Run Keycloak: Use the provided scripts to start the Keycloak server.
- Access Admin Console: Log in to the admin console using default credentials.
Initial Configuration
Once installed, configure Keycloak to suit your needs:
- Create a Realm: Realms are isolated management spaces within Keycloak.
- Add Users and Roles: Set up users and define roles for access control.
- Configure Clients: Integrate your applications by configuring clients.
Keycloak in Action
Real-world Use Cases
Keycloak is used across various industries to secure applications and manage identities. Common use cases include:
- Enterprise Applications: Secure internal applications.
- Customer Portals: Manage customer identities and access.
- Mobile Apps: Secure mobile applications with robust authentication.
Integration Examples
Integrate Keycloak with a wide range of applications and services, such as:
- Web Applications: Using Keycloak adapters for frameworks like Spring Boot and Node.js.
- APIs: Secure REST APIs with OAuth2 and OpenID Connect.
- Third-party Services: Integrate with external identity providers for SSO.
Authentication and Authorization
Understanding Authentication in Keycloak
Authentication verifies a user’s identity. Keycloak supports various methods, including:
- Password-based Authentication: Username and password login.
- Social Login: Use social media accounts to log in.
- Two-Factor Authentication (2FA): A second verification step for enhanced security is added.
Keycloak does not come with out of box SMS based OTP support. Which his arguably the most common method on internet. Refer to this gap we are comes up with the solution. Keycloak is something that can help any application developer to implement while developing the app. Here are some of the OTP+ feature I would like to callout.
Understanding Authorization in Keycloak
Authorization controls what resources a user can access. Keycloak uses role-based access control (RBAC), where roles are assigned to users, defining their permissions.
Here is a detailed blog on Authentication and Authorization.
User Federation
What is a User Federation?
User federation allows Keycloak to connect to external user stores, like LDAP or Active Directory, to pull user information. This means you can use your existing user databases without migrating data.
Benefits of User Federation in Keycloak
- Centralized User Management: Manage users from one place, even if they are in different databases.
- Seamless Integration: Connect easily with existing user stores.
- Enhanced Security: Combine Keycloak’s security features with existing user stores.
Single Sign-On (SSO)
Definition of SSO
Single Sign-On (SSO) allows users to access multiple applications with one set of login credentials. This improves the user experience and reduces the need for multiple logins.
How Keycloak Enables SSO
Keycloak acts as a central authentication server. Once a user logs in to Keycloak, they can access any connected application without logging in again, using token-based authentication.
Identity Brokering
What is Identity Brokering?
Identity brokering lets Keycloak act as an intermediary between users and external identity providers. This allows users to log in with credentials from services like Google or Facebook.
Keycloak’s Role in Identity Brokering
Keycloak simplifies identity brokering with built-in support for various identity providers. You can configure Keycloak to accept logins from these providers, making the process smoother for users.
Keycloak Security Features
Security Protocols Supported
Keycloak supports several security protocols, including:
- OAuth2: For authorization.
- OpenID Connect: An identity layer on top of OAuth2.
- SAML: For exchanging authentication and authorization data.
Ensuring Security with Keycloak
Keycloak offers features to ensure security, such as:
- Token Revocation: Invalidate tokens to cut off access.
- SSL/TLS Support: Encrypt data transmission.
- Auditing and Logging: Track authentication and authorization events.
Managing Users and Roles
User Management Features
Keycloak offers comprehensive user management features:
- User Registration: Allow users to create accounts.
- User Profiles: Manage user information and preferences.
- Account Recovery: Help users recover access to their accounts.
Role-Based Access Control (RBAC)
RBAC in Keycloak involves defining roles and assigning them to users. Roles determine access to resources, providing flexible permission management.
Admin Console and CLI
Using the Admin Console
The Keycloak admin console is a web interface for managing all aspects of Keycloak, including:
- User Management: Create and manage users.
- Role Management: Define and assign roles.
- Client Configuration: Integrate applications with Keycloak.
Command-Line Interface (CLI) Tools
Keycloak also provides CLI tools for configuration and automation. Use the CLI for tasks such as:
- Server Configuration: Set up and configure Keycloak.
- User Management: Add and modify users and roles.
- Scripted Operations: Automate tasks with scripts.
Extending Keycloak
Customization Options
Keycloak is highly customizable. You can:
- Theme Customization: Change the appearance of login pages and user interfaces.
- Custom Authentication Flows: Define custom authentication processes.
Extending Functionality with Plugins
Use plugins to extend Keycloak’s functionality. Develop custom plugins to add features or integrate with additional services, enhancing Keycloak’s capabilities.
Conclusion
Keycloak is a robust and flexible IAM solution that simplifies securing applications and managing user identities. With its comprehensive features, open-source nature, and extensive customization options, Keycloak is ideal for developers looking to enhance their security infrastructure. Although Keycloak is not comes with SMS based OTP support thats why you should use OTP+.