If you’re starting with digital security, you know how important Identity and Access Management (IAM) systems are. Keycloak is a well-known option, but some other great choices exist. Let’s look at the best alternatives to Keycloak, with their pros and cons, to help you find the right one for your needs. But before that, if you are not sure what Keycloak is, let me share a brief.
Introduction to Keycloak
Keycloak is an open-source Identity and Access Management (IAM) solution for modern applications and services. With its flexible, customizable, and developer-friendly architecture, Keycloak offers many features that streamline the authentication and authorization processes.
Keycloak Core Features
1. Single Sign-On (SSO)
- Cross-domain SSO
- Identity brokering
2. User Federation
- LDAP integration
- Custom user storage
3. Identity Brokering and Social Login
- Built-in providers
- Custom provider support
4. Fine-Grained Authorization
- Policy-based access control
- Resource-based access control
5. Centralized Management
- Admin Console
- REST API
6. Customizable User Interface
- Theme support
- Localization
7. Security Features
- Two-factor authentication
- Session management
- Audit logging
8. Extensibility and Customization
- Custom authentication flows
- Event listeners
Here are Keycloak features in detail, which you can follow.
Join us as we explore the top Keycloak alternatives to determine which is best for your security needs.
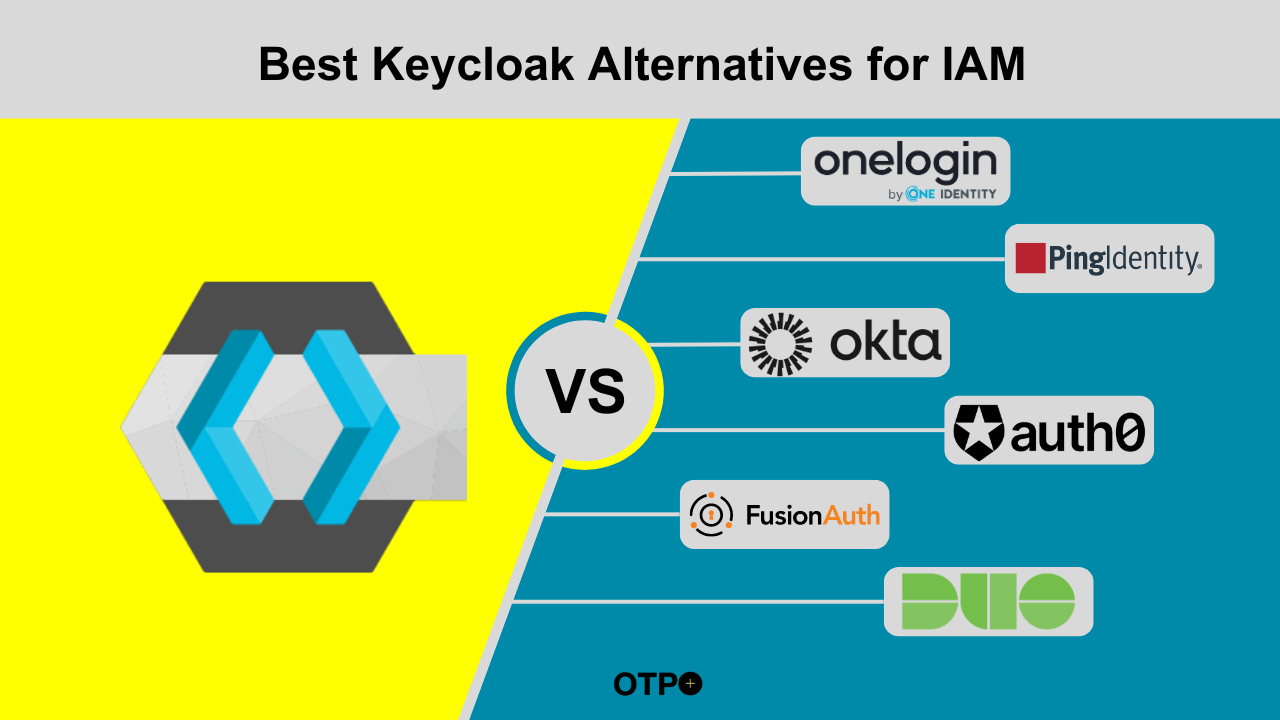
Best Keycloak Alternatives
Octa
Auth0
OneLogin
Ping Identity
ForgeRock
Microsoft Entra ID
Cisco Duo
FusionAuth
Top Keycloak Alternatives
1. Okta
Okta is a big name in cloud-based IAM. It’s packed with features and can scale to meet your needs. Whether you’re looking for single sign-on (SSO), multi-factor authentication (MFA), or automated user management, Okta has you covered.
Key Features
- Single Sign-On (SSO): Access multiple apps with just one login.
- Multi-Factor Authentication (MFA): Add an extra layer of security.
- Lifecycle Management: Automatically manage user accounts.
- Integration: Works with thousands of apps and services.
Notes: If you need clarification on what multi-factor authentication is, Here is the blog.
Pros
- Extensive integration options
- User-friendly interface
- Strong security features
Cons
- Can be expensive
- Complexity for small businesses
2. Auth0
Auth0 is super flexible and perfect for developers. It lets you customize your authentication and authorization processes, and it supports a variety of identity providers and protocols.
Key Features
- Universal Login: A customizable login experience for all your apps.
- Authentication API: Build custom authentication flows.
- Social Login: Easily add social media logins.
- Adaptive MFA: Security that adapts to the context.
Pros
- Highly customizable
- Excellent for developers
- Supports multiple identity providers
Cons
- It can get pricey with advanced features
- The steeper learning curve for beginners
3. OneLogin
OneLogin is a unified access management solution focusing on user experience and security. It works well with cloud and on-premises apps, giving users great flexibility.
Key Features
- Adaptive Authentication: Dynamic, risk-based security.
- SmartFactor Authentication: Contextual data for better security.
- Unified Directory: Centralized user management.
- Comprehensive Integrations: Works with many apps and services.
Pros
- Easy to use
- Strong integration capabilities
- Good balance of security and usability
Cons
- Occasional issues with customer support
- It can be expensive for small organizations
4. Ping Identity
Ping Identity offers advanced IAM solutions focused on security and compliance. It supports many authentication methods and provides strong access controls.
Key Features
- Single Sign-On (SSO): Easy access to multiple apps.
- Multi-Factor Authentication (MFA): Strong authentication options.
- API Security: Manage and protect API access.
- Identity Governance: Ensure compliance with governance policies.
Pros
- Strong security features
- Good compliance support
- Flexible authentication methods
Cons
- Can be costly
- Requires technical expertise to set up
5. ForgeRock
ForgeRock offers a robust identity platform for enterprises. It provides comprehensive tools for managing identities, securing access, and ensuring compliance across your digital ecosystem.
Key Features
- Identity Gateway: Manage and secure access to APIs and services.
- User-Managed Access (UMA): Let users control their data.
- AI-Driven Analytics: Use AI to detect and respond to threats.
- Scalability: Built to grow with your organization’s needs.
Pros
- Comprehensive identity management
- Strong security features
- Scalable for large organizations
Cons
- Can be expensive
- Requires technical expertise
6. Microsoft Entra ID
Microsoft Entra ID, previously known as Azure Active Directory, is tightly integrated with Microsoft’s cloud services. It offers robust identity management and access control for hybrid environments.
Key Features
- Conditional Access: Set policies based on user, device, and location.
- Identity Protection: Detect and address identity risks.
- Self-Service Password Reset: Let users reset their passwords.
- Microsoft Integration: Works seamlessly with Office 365 and Azure.
Pros
- Seamless integration with Microsoft products
- Strong security features
- Good for hybrid environments
Cons
- Complexity for non-Microsoft environments
- Can be expensive
7. Cisco Duo
Cisco Duo simplifies and enhances multi-factor authentication. It’s user-friendly and quick to deploy, making it a favorite for organizations looking to boost security without too much hassle.
Key Features
- Multi-Factor Authentication (MFA): Easy-to-use second-factor authentication.
- Device Trust: Ensure only trusted devices can access your apps.
- Adaptive Authentication: Context-aware access policies.
- User-Friendly: Intuitive interface and seamless user experience.
Pros
- Easy to deploy and use
- Strong security features
- Good user experience
Cons
- Limited features beyond MFA
- Can be costly for larger deployments
8. FusionAuth
FusionAuth is excellent for developers looking for a customizable IAM solution. It’s designed to be easily integrated into any app and offers robust security without sacrificing flexibility.
Key Features
- Customizable Workflows: Tailor authentication flows to your needs.
- User Management: Full control over user accounts.
- Localization: Supports multiple languages and regions.
- Extensible: Add functionality with plugins and APIs.
Pros
- Highly customizable
- Developer-friendly
- Good for international use
Cons
- It can be complex to set up
- Limited support for non-developers
Conclusion
Choosing the right IAM solution is key to keeping your organization secure and running smoothly. While Keycloak is a solid choice, alternatives like Okta, Auth0, Centrify, OneLogin, Ping Identity, Microsoft Entra ID, Cisco Duo, FusionAuth, and ForgeRock offer diverse features that better fit your needs. Take the time to explore these options and find the perfect IAM strategy for your goals. Also, if you are going to start developing a Keycloak extension, then you must read this blog that shows some tips for developing Keycloak extensions.